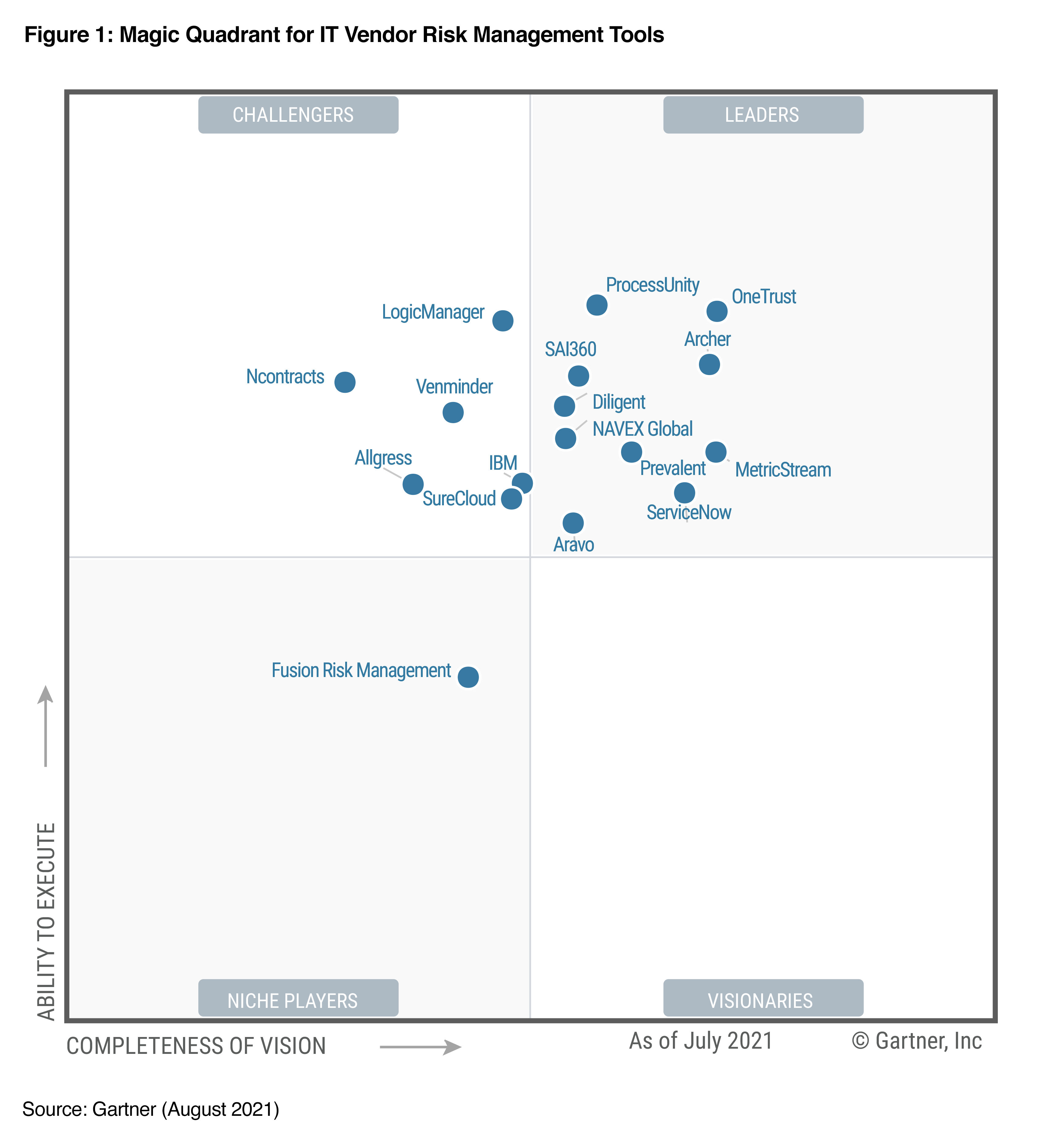
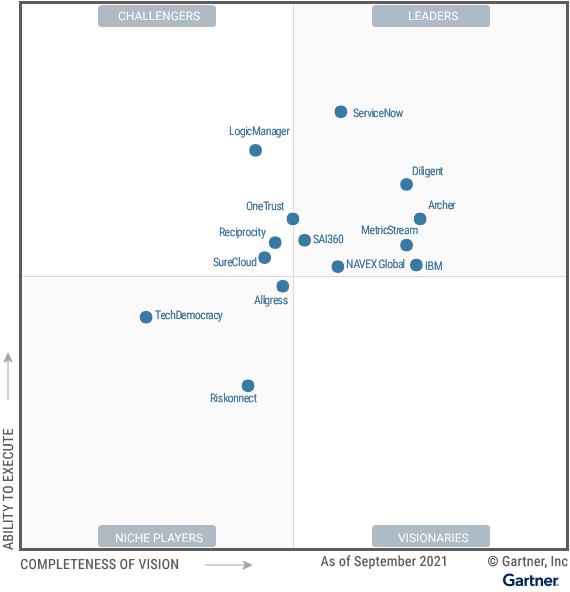
Vendor risk management (VRM) is an important part of the overall risk management landscape for enterprise organizations. Most corporations have thousands of suppliers: Walmart, for instance, counts more than 100,000 vendors among its ranks. These suppliers are responsible for everything from software to the product supply chain to vital infrastructure needs.
Your company’s security and reputation are only as good as its weakest link, so it’s vital to ensure that all of your suppliers are held to high standards and monitored regularly for compliance.
Third-party risk categories
Third-party vendor risks fall into a range of categories:
- Cybersecurity: How robust is the cybersecurity defense posture of your vendors? A data breach can leave your proprietary or customer data vulnerable, so it’s essential to make sure that each vendor has strict cybersecurity protocols in place to minimize the likelihood and outcome of a breach. You should hold each vendor to, at a minimum, the standards that you set for your own organization, with expectations clearly set out in your contract via an Information Security Addendum.
- Compliance: It’s important to ensure that any regulatory requirements that your organization needs to abide by—such as data storage policies and regulations related to any part of your business that the vendor touches—are also honored by your vendors.
- Reputational risk: Any public incident around a vendor can also impact your organization’s reputation. This covers a wide range of incidents, which could include violations of laws or regulations, loss of customer data due to negligence or data breach, or controversial statements by the CEO.
- Financial risk: Is a vendor likely to become financially insolvent or go out of business? This can hurt your company significantly by causing an unexpected interruption of services, or a break in your supply chain. This could mean that your organization wouldn’t be able to fulfill its contractual obligations to customers, causing a loss of revenue and damage to your reputation.
- Operational risk: How likely is it that the vendor wouldn’t be able to fulfill their obligations to your organization? If this happened, how would it impact your daily operations? Make sure that you are aware of your vendors’ business continuity plans, and that your business has its own continuity plan. (Read more on how COVID-19 is impacting third-party risk.)
- Strategic risk: Do the vendors’ decisions align with your own organization’s strategic objectives? This might include decisions around technology use, or even ethical questions. Make sure that your organization has a thorough understanding of your vendors’ values and long-term plans to ensure they work with yours.
A vendor risk checklist
A VRM checklist might include items such as:
- Conduct an audit of what types of employee or customer data each vendor needs access to, and make sure that their access is limited to that scope
- Review each vendor’s contracts and policies to check for compliance issues with your own standard policies and industry requirements, and ask for accommodations if necessary
- Review each vendor’s cybersecurity protocols and determine whether they comply with industry requirements and your own organization’s guidelines
- Assess the level of potential harm to your organization or customers in the event of a breach via a vendor, and determine whether mitigation strategies may be necessary
- Review each vendor’s incident response plan
- Evaluate each vendor’s business continuity plan
- Monitor each vendor for credit risk and bankruptcy filings
Manually managing vendor risk
In many organizations, compliance managers would likely go through a line-by-line inventory of vendor compliance requirements. They would also conduct interviews with each vendor to determine whether their policies are in line with the organization’s policies, and conduct on-site audits to assess the work environment. This process is time-consuming and ripe for error, and it often results in duplication of work, as employees from different departments may conduct similar audits without sharing information.
In addition, responses often can’t be trusted: RiskRecon found that only 14% of risk practitioners trusted that third parties’ security precautions matched the self-reported responses from their questionnaires. In fact, 31% of respondents said they had vendors that they considered a material risk in the event of a breach.
With a manual process, most VRM is done purely during the onboarding stage and then at timed intervals, which may only be quarterly or once a year. Apart from these occasions, your organization may be left in the dark regarding changes to your vendors’ technology, financial performance, or business strategy. When manual processes are used, there’s a lack of visibility into the ongoing status of your vendors’ compliance and other risk factors that may leave your own organization vulnerable.
Shifting to an automated VRM process
Many forward-thinking organizations are making the shift to a VRM process that’s driven by artificial intelligence and automation. An automated VRM process will substantially reduce the amount of manual labor required by your team, and provide opportunities to partake in continuous monitoring, enabling you to identify risk triggers early. This way, you can remediate them before they cause potential harm to your organization.
An automated VRM solution should:
- Pre-qualify vendors
A high-quality solution should integrate data that checks a prospective vendor’s security performance before you commit to working with them, so you can rule out those with security concerns. - Classify vendors according to risk level
Although only certain vendors will need access to proprietary data or touch your infrastructure, this subset of vendors requires careful monitoring. Your solution should identify these vendors on your behalf. - Automate compliance and risk assessment with self-reporting tools
Your solution should provide a variety of onboarding forms and questionnaires, ensuring that every vendor is up to date on compliance requirements. It should also provide automated follow-ups and provide alerts when compliance issues arise in a vendor’s response. - Provide continuous risk monitoring
Your solution should track SLAs with real-time performance monitoring, provide real-time financial intelligence and other data feeds, track audit findings from on-site visits, and integrate with security rating services to categorize vendors and automate audit schedules. - Provide third-party risk reporting
Your solution should provide a clear analytics dashboard, showing your vendor risk landscape at a glance, with vendor risk scorecards to showcase potential security gaps.
By making the shift to an automated VRM solution, you’ll be able to cut down on manual and repetitive work to track compliance, and gain access to real-time data that will help you determine when risk levels are elevated for any vendor. Moving to an automated system will help you move beyond mere compliance into continuous risk monitoring, giving your organization the data intelligence it needs to detect new risks early and to mitigate them immediately. With an intelligent, automated VRM solution, your organization will be able to streamline and enhance its overall risk management process.
Checklist:
Vendor Risk Management Solution Checklist
This checklist outlines key features you should look for in a VRM solution and explains the significance of each in mitigating vendor risk, including:
- vendor risk assessment workflows
- vendor engagement
- risk reporting requirements
- architecture & infrastructure