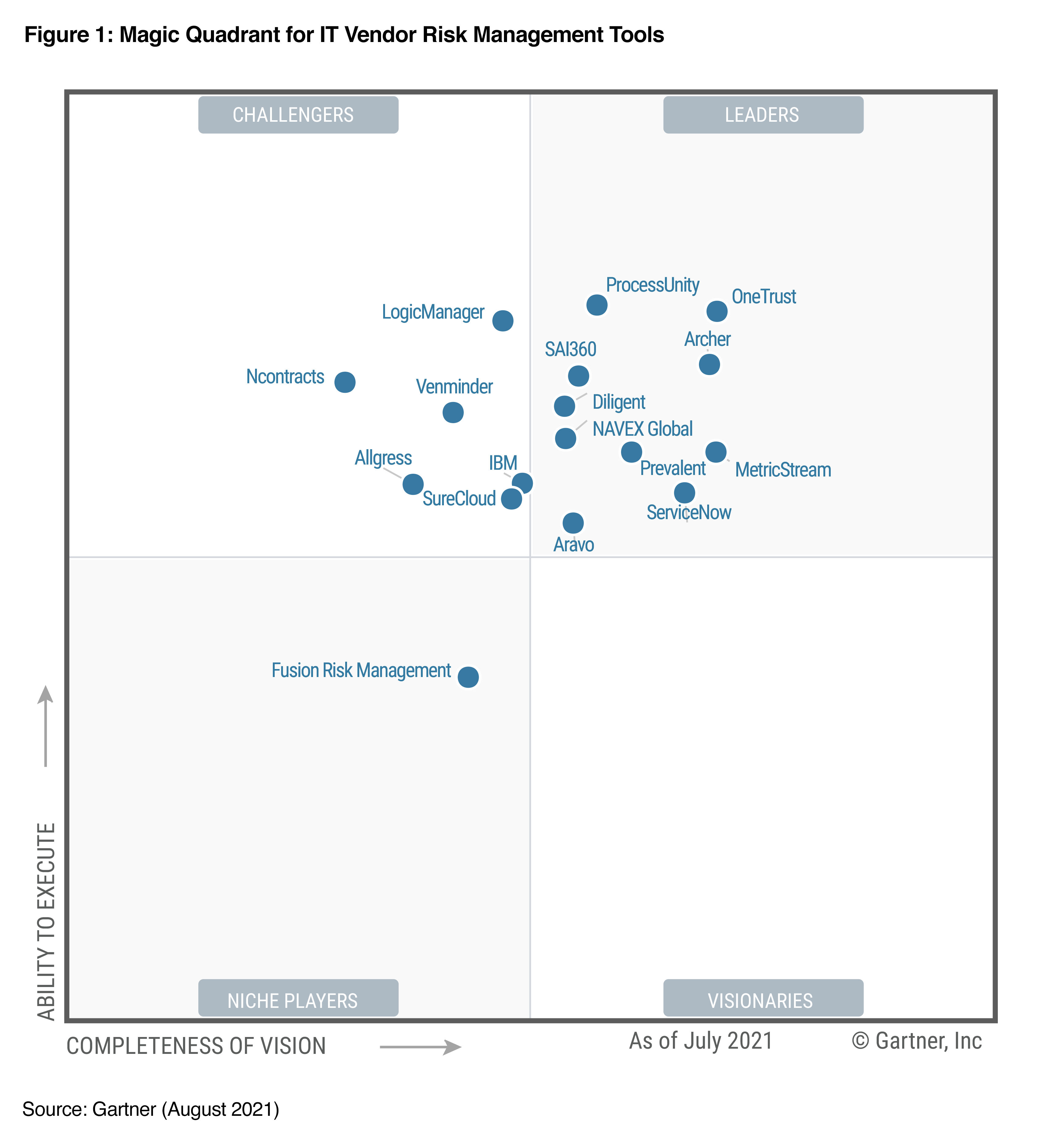
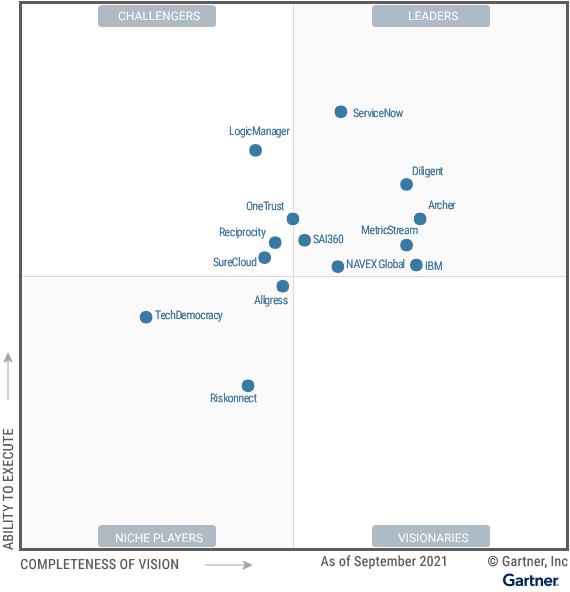
Data breaches can cause significant damage to your business, but not if you learn how to implement strong controls to prevent this organizational risk.
Facebook, British Airways, Uber, Verizon, and over 140 US-based universities have all recently suffered massive data breaches and, as a result, irreparable monetary and reputational damage.
Every new data breach teaches us that IT governance is critical and data breaches must be looked at as an organizational risk, rather than exclusively an IT risk. After all, they have the power to totally disrupt operations, impacting the bottom line.
Vulnerabilities exist in every organization
According to Wired magazine’s Worst Cybersecurity Breaches of 2018, a group of Iranian hackers infiltrated 144 US-based universities through spear phishing emails.
These emails were highly targeted. They tricked professors and other university affiliates into clicking malicious links and entering login information. Before you knew it, the suspected hackers had their hands on over 31TB of data.
How does this sort of thing happen for these large, well-known universities—with data privacy officers, data protection managers, IT compliance managers, or infosec managers? And more importantly, how can it be prevented?
Identify your specific threats and controls
You might not be the size of Facebook, and maybe your IT team is significantly smaller than Uber’s, but there are some general IT governance best practices you can implement to stop your data from falling into the hands of unauthorized individuals.
The first step is to identify your threats. In the case of this blog post, we’re focused on data breaches, so some examples that could result in a data breach include:
- Systems and network devices use out-of-date, potentially vulnerable software.
- Inappropriate manual intervention causes unauthorized changes to programs or data.
- Inappropriate access leads to unauthorized changes to systems or programs.
Those are just a few examples. There are countless resources to help you with threat identification, from simple reference lists like this one from Advisera, to advanced threat intelligence platforms.
Once you’ve identified potential threats, you should identify and implement the controls that follow.
Some sample controls based on the threats listed above could include:
- Ensuring system software patches and upgrades to server systems and network devices are applied.
- Employing a defense-in-depth strategy for cybersecurity and implementing critical systems to help prevent known threats and vulnerabilities (i.e., anti-malware, anti-virus, encryption, data loss protection, firewall, VPN, etc.).
- Authenticating the identity of users and ensuring the proper maintenance of these user profiles so that new contractors, terminations, and role changes are always up to date.
Continuously monitor controls
Next, you’ll need to test your controls to make sure they’re working effectively to mitigate your identified threats. If you use traditional monitoring methods, the process can be both time consuming and prone to error.
But it becomes much easier when you connect your data sources in a single platform like HighBond, and employ analytical techniques for automated testing. And for those of you who aren’t scripting wizards, HighBond has pre-built scripts to run countless tests.
Based on the controls we mentioned before, here are a few tests to consider:
- Failed login trends: Identify how many times a user has failed to login and flag the instances that might require further examination.
- Password expiration: Find those user accounts where the password age exceeds the expiration policy.
- Dormant accounts: Locate user accounts that have been inactive for an extended period of time.
Setting these control tests to run on a regular basis (continuous monitoring) will help to make sure you’re staying on top of your controls. You’ll know right away when something suspicious needs your attention.
Refine and expand your program
Identifying and prioritizing threats, and continuously monitoring the effectiveness of IT controls leads, will keep you confident in your organization’s cybersecurity.
This data-driven approach means that you’ll be able to quantify risk and focus your efforts as well as your limited resources. And over time, your program will become more sophisticated, which means you’ll know which areas require more attention.
The final piece of the puzzle is to integrate the technical elements of your cybersecurity program (discussed above) with your overall IT risk landscape. Once you’ve achieved that, you can start looking to align it with the organization’s top-level enterprise risk management framework. Cybersecurity is regularly cited as one of the key risks on every board’s agenda and because of that, it needs to be effectively managed, both bottom-up and top-down.
Of course, all of this is made so much easier when you use a purpose-built tool. Visit the HighBond page to learn more about how we can help you get started.
White paper:
KRI Basics for IT Governance
You’ll learn:
- The different kinds of indicators, what they measure, their purpose, and audience
- How KRIs fit into a greater IT risk management program
- How to select your own KRIs, including a worksheet
- How to ensure your KRI program is scalable and sustainable.