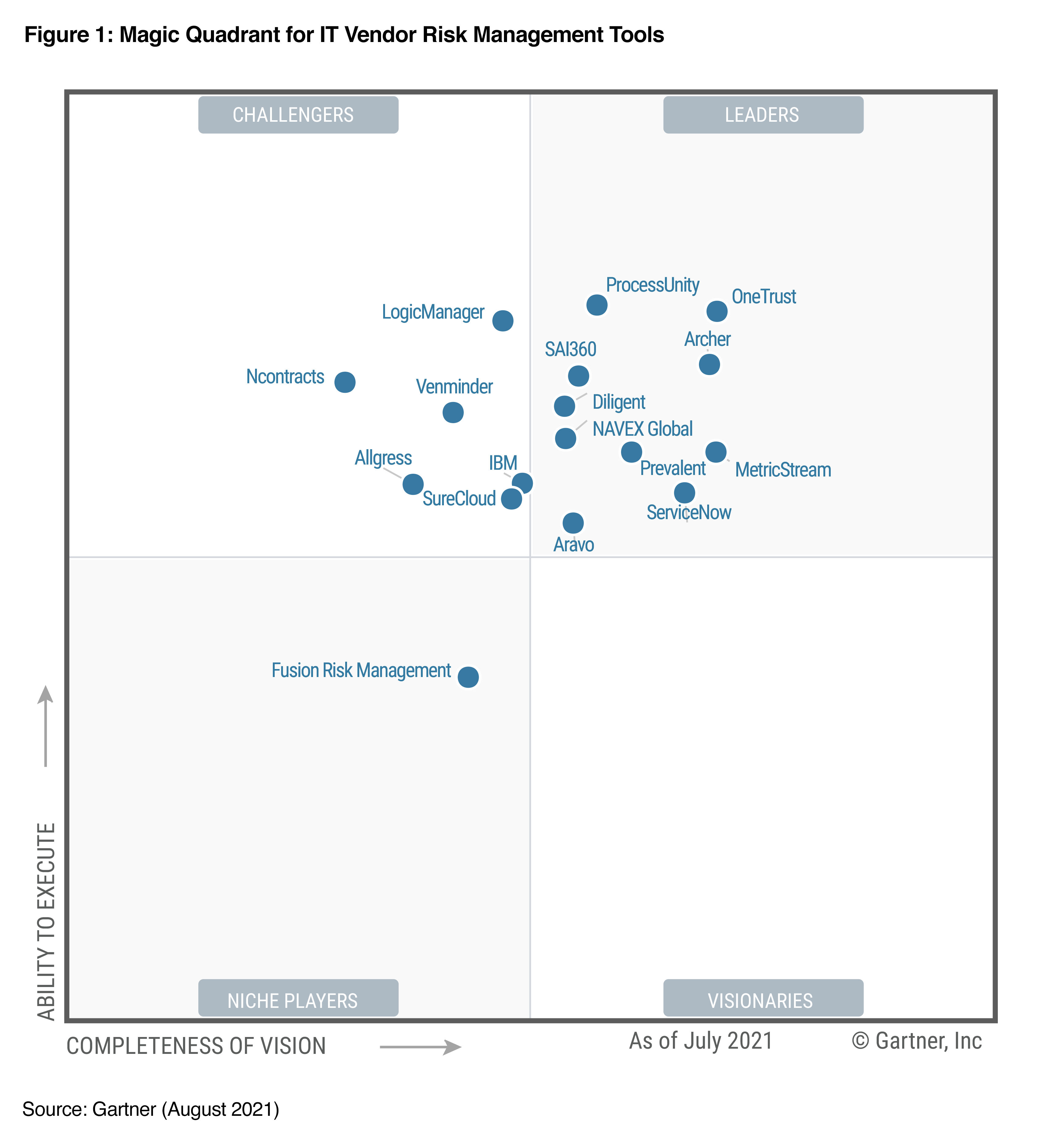
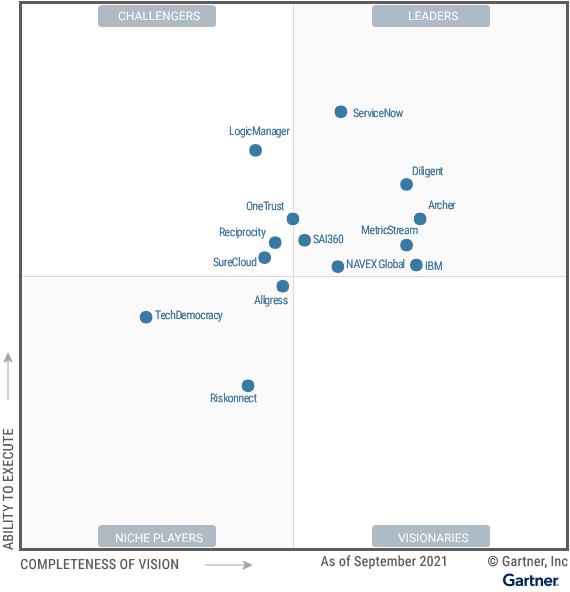
With so many IT responsibilities to juggle, how can you make sure you’re ready for an audit at any given time? Here are nine steps you can take to make sure you’re prepared.
As an IT manager, you’ve got a long list of responsibilities—and as the major hub of almost any organization, it’s not surprising that between regulations, risks, controls, and frameworks, things can get pretty complicated.
Sure, it requires some upfront work, the right people, and of course, the right technology, but when you’re IT audit ready, you’ll spend less time actually dealing with audits and have more time available for mission-critical work.
“Being audit ready means you’re managing your IT risks, dealing with security, controls, and compliance, and you’ve done the necessary work to avoid any unpleasant surprises in an IT audit report. Everything is in place for the auditors to come in and do their job.”
9 steps to IT audit readiness
These steps will help give you an idea of the path towards IT audit readiness.
1. Identify, assess, and classify IT risks
First, you need to know what risks your IT department faces. Unauthorized systems access is one example. Looking at all of your IT assets, both tangible (information) and intangible (reputation), determine what could be compromised.
Now classify your risks by impact: low, medium, or high. This will help you prioritize which to tackle first. Read more about assessing low, medium, and high-priority risks.
2. Identify controls
With your list of risks defined and prioritized, it’s time to pair them with controls. Starting with the risks that you identified as high impact, find ways to mitigate or manage the risk—these are your controls. A control in the previous unauthorized access example would be a firewall to prevent external system access.
3. Map controls to a master framework library
How many of your controls also tick a box in the current frameworks followed by your organization? In the above example, the control (making sure anyone who logs into the system remotely has proper authorization) will mitigate the risk (data breaches), which also mitigates the enterprise risk (reputational and strategic). But this is also a required control in order to be SOC compliant. So you’re essentially killing two birds with one control.
4. Plan, scope, and stress-test micro-risks
Controls are designed to address risk at many levels. The very detailed and specific risks are known as micro-risks. At this level, you can plan out the exact details of your controls, including cost, process, timing, and resources. Let’s go back to the example of external system access. A control might be to implement a system that requires two-factor authentication. Scope the cost, security requirements, and implementation of the control and then determine if that’s the right solution for your organization.
5. Assess effectiveness of existing controls
Your controls are now active, but are they operating as expected? There’s a few ways to test this. First, use analytics to query your data and spot problems, like identifying high-risk passwords that are set to never expire. And the second way to test your controls is by sending self-assessment surveys and questionnaires to control owners.
6. Capture, track, and report deficiencies
When you find a control that isn’t working as expected, it’s important to act fast. In many cases, recurring data analysis can be used to strengthen controls or add an extra layer of control. For example, if controls over access to sensitive data aren’t fully effective, you can use regular data analyses to find instances of risky access. By finding this early and often, you can deal with it before it becomes a major issue.
7. Monitor and automate testing of controls
Daily, weekly, or monthly monitoring using analytics means you’ll always be up to date on how effective your risk management and control activities are. It will vary by organization, but common IT activities that can be monitored include use of admin and special systems access, firewall changes, segregation of duties, physical access logs, or remote access logs.
8. Flag exceptions, review, investigate, and remediate
During this step, often called exception/issue management, you’d take the issues identified from your automated testing and weed out the false positives from the actual control breakdowns. Once you have your control breakdowns isolated, you’ll action them. This could include various forms of remediation including restricting or revoking access to systems or data, or changing the control to mitigate the chance of this breakdown happening again.
9. Ongoing improvement of processes
This is the final step in your journey toward IT audit readiness. It’s the constant tweaks and improvements that will be made over time as your program matures. This practice will result in a reduction of risks over time and an improvement of your control process through ongoing testing, monitoring, and addressing the exceptions.
Congratulations! You’re now in that highly coveted state of IT audit readiness!
eBook
9 steps to IT audit readiness
You’ll learn how to:
- Identify and assess IT risks and map them to controls
- Plan, scope, and stress-test micro risks
- Assess the effectiveness of existing controls
- Capture, track, and report deficiencies
- Create a continuous cycle of testing, monitoring controls, and addressing exceptions.