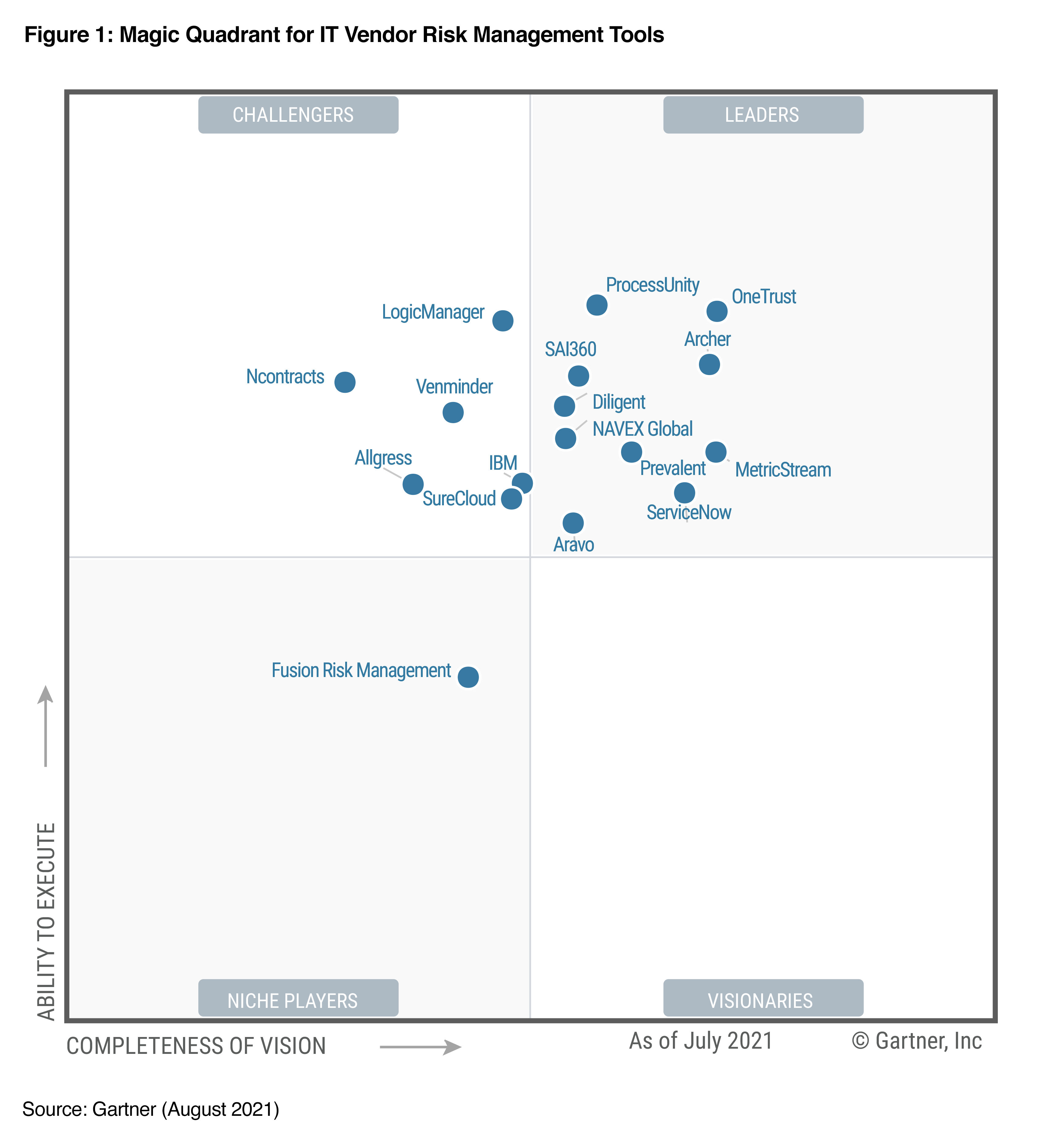
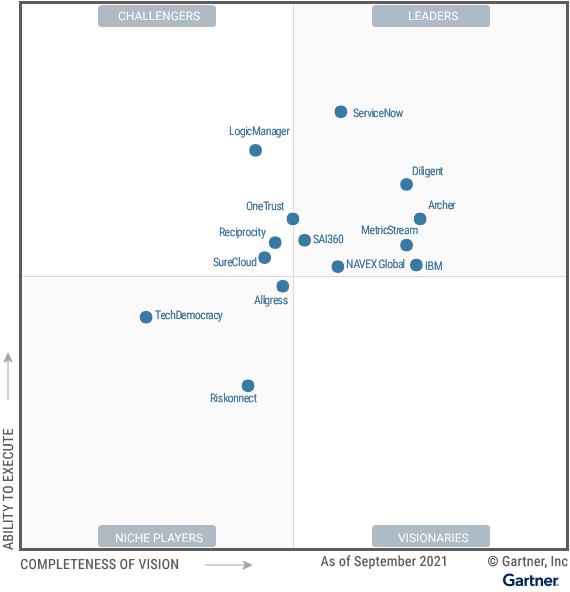
Third-party risk management is a hefty responsibility, with threats and challenges coming from all directions. And that’s just the dangers you know about! But rather than fearing the unknowns, learn where and how to find them.
Outsourcing to third parties is pretty much inevitable for modern organizations. But with this convenience and cost reduction comes great responsibility. To avoid the risks that cause financial and reputational damage, you need to be extra vigilant about the companies you’re doing business with.
According to Ponemon Institute’s 2018 data risk study, 59% of companies have experienced a data breach caused by a third-party supplier or partner. And 22% admitted they were unaware of any third-party data breach in the past 12 months. So what unknown risks are flying under your radar?
To help you answer that question, we’ll look at some of the reasons risks remain hidden, and how to bring them to the surface of your risk management program.
“There are many valuable—but often unused—data sources that can bring third-party misconduct to light.”
The origin of “unknown unknowns”
You may remember then U.S. Secretary of Defense Donald Rumsfeld’s take on the limitations of intelligence reports at a 2002 news briefing, He said: “There are known knowns. There are things we know we know. We also know there are known unknowns. That is to say, we know there are some things we do not know. But there are also unknown unknowns, the ones we don’t know we don’t know.”
So how can you move from a place of uncertainty to one of understanding? By being aware of—and embracing—what you don’t know.
Rumsfeld’s tongue-twisting approach can be applied to many things in life, including third-party risk management, which has gotten cloudier in recent years because of:
- Globalization, causing organizations to source supplies far from home. There are multiple new risk considerations, from anti-bribery and corruption laws to potential supply chain disruptions caused by political unrest.
- Emerging technologies like the internet of things (IoT) and machine learning, which aren’t well understood by many organizations (nor heavily regulated yet).
- An increase in cyber attacks, from phishing to ransomware.
- Ever-changing regulations like the GDPR, which came into effect in 2018 and dictates the data privacy obligations of organizations who deal with the personal data of EU citizens.
- Fourth-party risk, which is your third parties’ outsourcing to third parties. This adds an extra layer of risk to worry about.
You need to think outside the tick-box to have a truly effective TPRM program. Start by diving into the “unknown unknowns.”
Get to know the things you don’t know
One of the main challenges in identifying and managing third-party risk is that most organizations tend to default to managing the “known knowns.” These are things like your:
- Vendor master file
- Third-party onboarding requests
- Accounts payable file
- TPRM via GRC program.
While these are important, you also need to think outside the tick-box to have a truly effective TPRM program. Here’s how to do that by diving into the “unknown unknowns.”
1. Identify your stakeholders.
Find critical stakeholders across the organization and enlist them to support the ongoing success of the program. You need to increase awareness at all levels of the business, so everyone starts integrating good TPRM practices into day-to-day processes. (Board-level involvement is also essential for stakeholder buy-in.)
While you’re doing this, include some non-traditional stakeholders. By shifting your expectations and pulling in different areas of expertise, you’ll foster a richer risk management culture. Ask people questions around corporate objectives and goals, rather than on processes, and you’ll engage people you might not have even considered before.
2. Put a committee behind the wheel.
If only your CISO or supply chain leader is invested in what you’re doing, you’re missing the mark. Do you have enough mindpower driving your program? Do the people you’re relying on carry enough weight in the organization to move things forward? A committee that brings together compliance officers, privacy officers, and audit teams, for example, can enable you to fly far beyond your “known knowns.”
Once you’ve built your committee, find a community. By aligning with industry groups, you can share thoughts and ideas with likeminded people to keep on building a more robust TPRM solution.
3. Focus on the bigger picture.
It’s time to acknowledge you have blind spots. For example, many organizations are looking so closely at vendors, they don’t see the risks that brokers, partners, or financiers pose.
Here’s an idea: challenge your committee to come up with an inventory of risk events and scenarios that third parties bring to your organization (e.g., a data breach). Then, map those to the types of third parties that could expose you to that risk (e.g., your payroll company). As you brainstorm, chances are you’ll come up with novel types of risk to consider (e.g., an improperly offboarded vendor still receiving automated customer data updates).
This exercise will help you clearly define the scope of your TPRM program. And if used with a tool like ThirdPartyBond, you’ll gain deeper visibility into the entire third-party risk management lifecycle.
4. Don’t miss what’s right in front of you.
There are many valuable—but often unused—data sources that can bring third-party misconduct to light. Ask the stakeholders in your committee if they have data you can use around:
- Threat and vulnerability management
- Data loss prevention
- Identity and access management
- Security incident and event management.
There are many more sources of untapped information in your organization. Start digging, and you might be surprised what you find in previously overlooked data.
To hear more about “knowns” and “unknowns,” along with some crazy real-world third-party risk stories, tune into the Office Hours episode on third-party risk management, featuring Chris Murphey, Senior Product Manager at Galvanize.
A framework for better understanding
An understanding of all risks—even the ones that are out of your direct control—is key to a mature risk management program. Using this framework can enable you to start recognizing the unknowns in your organization. As you assemble the right people, processes, and technology, you’ll be equipped to grow your third-party risk management program beyond anything you’ve ever known.
eBook:
Third-party risk management essentials
This eBook explores the:
- Basics of third-party risk management.
- Difference between TPRM and vendor risk management.
- Process of picking a risk management framework that best fits your organization.