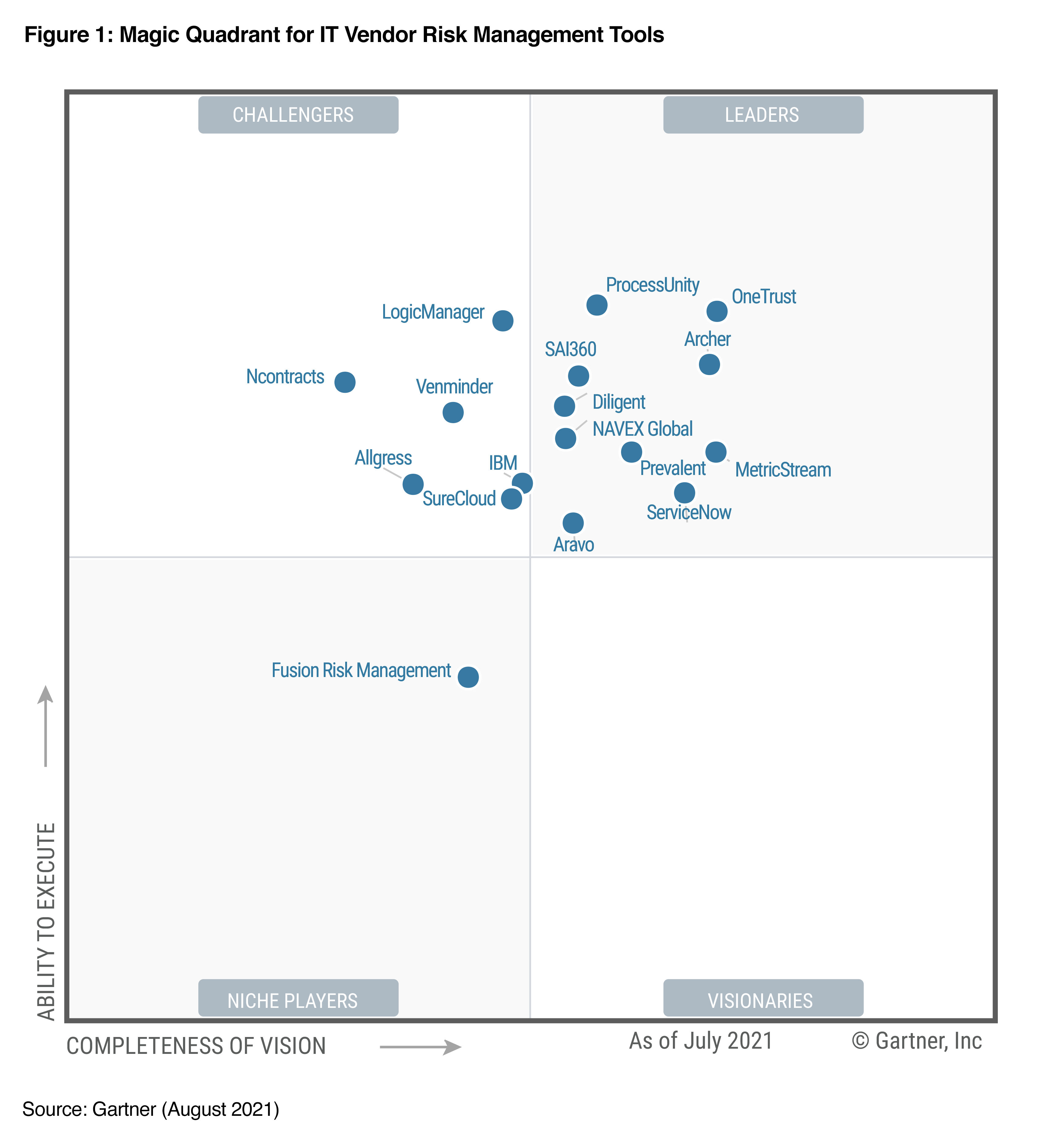
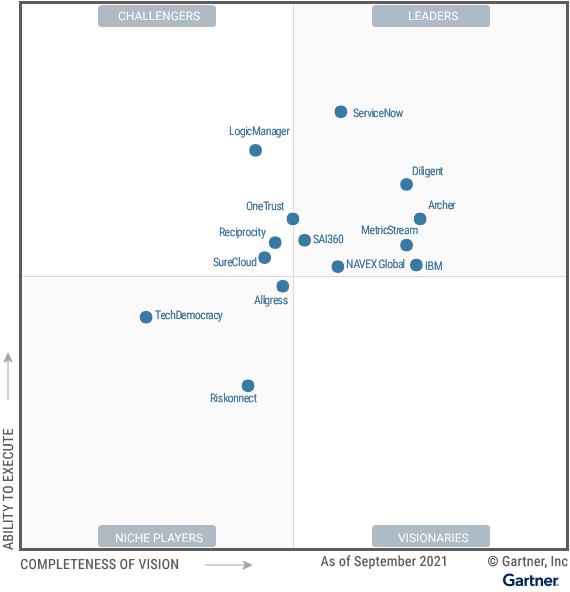
Third parties help organizations better serve customers, grow revenues, and cut costs. But they can also cause serious damage if you don’t properly manage your extended enterprise.
Some examples of third parties include your office’s paper shredding company, the food suppliers who stock your workplace cafeteria, and the SaaS company that stores your customers’ data in the cloud. When you trust your facilities, networks, and/or data to any of these third parties, you’re opening up your organization to potentially devastating financial, reputational, regulatory, operational, and strategic consequences. How?
Here are a few scenarios:
- The paper shredding company doesn’t securely dispose of your confidential data, and it’s stolen from a recycling bin.
- The food supplier doesn’t train staff on safe poultry handling techniques, and a number of your employees get sick.
- The SaaS company that stores your data in the cloud gets hacked, putting your clients’ information into the virtual hands of cybercriminals.
Third-party risk management challenges
Third-party risk management (TPRM) is obviously important, but many organizations aren’t doing it effectively—or extensively enough. There are various reasons why, including:
- Teams and resources are already stretched to capacity.
- The expectation that the third party itself is taking the necessary steps to manage risk.
- Uncertainty around how to implement a functioning vendor risk management (VRM) strategy and the true cost of ownership, which includes the logistics of ongoing maintenance and continual vendor assessment.
- A lack of buy-in from senior leadership.
“To ensure strategic alignment and resources, you need leadership commitment and executive support. Find the business leaders who can champion adoption.”
Five steps to kick off your TPRM program
Whether you’re just beginning your TPRM journey or want to improve an existing program, here are some starting points:
1. Identify your key risks
It’s crucial to uncover both internal and external threats across your organization. For example:
- Do you need to meet certain regulatory requirements (e.g., the Health Insurance Portability and Accountability Act (HIPAA))?
- Do you use a cloud provider to store customer data?
- How many employees have access to company or customer information?
- Could natural disasters or political unrest disrupt your supply chain?
2. Think of TPRM as an enterprise-wide endeavor
To ensure strategic alignment and resources, you need leadership commitment and executive support. Find the business leaders who can champion adoption. You need to increase awareness and integrate TPRM practices into day-to-day processes. Board-level involvement is essential for stakeholder buy-in.
3. Develop risk categories
According to the Opus & Ponemon Institute’s 2018 Third-Party Data Risk Study, organizations, on average, share confidential and sensitive information with approximately 583 third parties. That’s a lot of data to patrol!
However, it’s unlikely that you’ll need to treat each third party with the same scrutiny (e.g., an event caterer is low-risk, while your payroll provider is high-risk). You can start with a mini-survey of all of your vendors to understand the risk classification that you want to have for each. Once you identify those risk profiles, the next step is to identify a subset of high-risk vendors to examine more closely.
4. Complete a vendor risk management checklist
This is a simple way to identify your needs and software requirements to execute your program. Our vendor risk management checklist outlines key features you should look for in a VRM solution and explains the significance of each in mitigating vendor risk, including:
- Vendor risk assessment workflows
- Vendor engagement
- Risk reporting requirements
- Architecture and infrastructure
5. Pre-qualify vendors
Galvanize has integrated BitSight Security Ratings into ThirdPartyBond. These Security Ratings are similar to consumer credit scores (they range from 250 to 900) and are updated daily. That means that you can check the security performance of a potential vendor before you sign a contract, and during the entirety of your working relationship.
Third-party risk is getting more complex
Third-party risk management will only get more complicated as organizations increasingly outsource services (which often brings fourth-party risk management into the mix) and rely more heavily on technologies like the cloud to manage sensitive data.
You should never make the assumption that a third party is taking the necessary steps to mitigate threats. TPRM is your responsibility. It’s also an ongoing process; success will depend on continued collaboration among your business, security, and risk teams.
eBook:
Third-party risk management essentials
This eBook explores the:
- Basics of third-party risk management.
- Difference between TPRM and vendor risk management.
- Process of picking a risk management framework that best fits your organization.